13. Digital Forensics
Digital Forensics
ND545 C3 L4 A07 Digital Forensics
Overview
When an attacker is able to breach security, you need to understand what they did and retrace their steps. Digital forensics enables security professionals to conduct investigations into breaches whether from external or internal threat actors.
What is digital forensics?
Digital forensics is the application of computer science and investigative procedures involving the examination of digital evidence. The process includes collecting, preserving, analyzing, and reporting on evidence.
Digital forensics is a highly sensitive area. It should not be attempted without core expertise—one wrong move when collecting evidence, and an entire case can be destroyed. For example, sending a general security expert without specific DF expertise to assess a digital crime scene could result in the accidental deletion of evidence and more. A common misconception in DF is that forensics experts can look into anything and everything in the company when there is a cybercrime or breach. This is not the case. For example, if a df expert is brought in with a warrant to search an employee computer for evidence of digital fraud, that may be the only thing they have permission to search for. If they come across evidence of other unrelated activities, they’d have to get additional permission/warrants or revisit the scope of the investigation before gathering the evidence. One exception to this rule is in the discovery of child pornography, which is typically required to be reported to authorities immediately. The bottom line is that digital forensics efforts must be highly focused to ensure the right assets are investigated, and the appropriate evidence gathered.
Digital Forensics Process
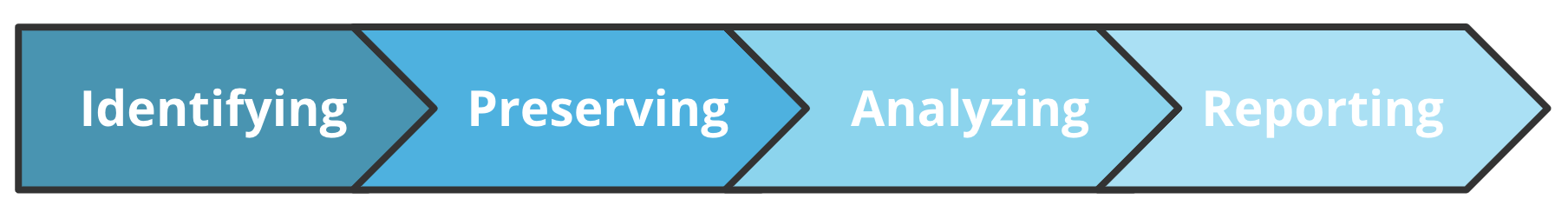
Identifying – This is the practice of finding and collecting the suspected original source or asset believed to contain evidence. (Example: The investigator has pinpointed a suspicious IP address belonging to the laptop in Ohio. The digital forensics investigator may have a co-worker send them the suspected laptop for analysis.)
Preserving – This is the practice of ensuring the integrity of the collected evidence and preserving a "digital trail" of the data or media. (Example: It's essential to monitor how the computer and any copies of data have been handled since being taken from the employee, along with who had access.)
Analyzing – This is the investigative portion of the process where a forensics practitioner begins looking into the acquired asset or medias data to find evidence of the suspected crime. (Example: The investigator may look through documents, email and chat conversations, browser website history, hard drives, and other user activities.)
Reporting – This is the process of creating a report of findings from the investigation for presentation to stakeholders and, in some cases, an attorney or jury in court. Reporting must also be tailored to the audience. In a court case where the jury is not technically savvy, findings must be explained in ways that are easy to understand for everyone. Failure to do so might render even the most irrefutable evidence ineffective. (Example: A digital forensics investigator may debrief a company's technical leaders in detail and then give a high-level summary to the general manager.)
Reference: https://blog.veriato.com/the-evolution-of-digital-forensics